- BTI Group
- Case Studies, IT Products Services Articles
- 2 min read
Protecting Businesses from Rapidly Multiplying Cybersecurity Threats

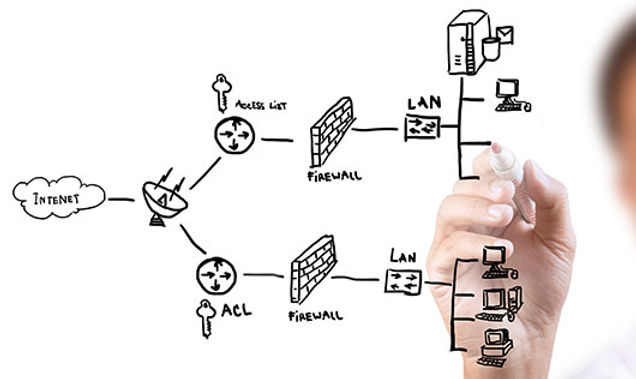
Against such increasingly sophisticated threats, standard internet security software, backups, and stand-alone monitoring devices, such as firewalls, password managers, and antivirus software, are increasingly insufficient.
As an alternative, a growing number of businesses are cost-effectively protecting against hacks by outsourcing to professional, third-party firms that remotely and continually provide layers of protection with a more comprehensive, integrated IT approach.
This strategy, which integrates both online and physical security monitoring, can continually deter and detect hacks as well as help businesses quickly respond and recover in the case of an intrusion. This eliminates the need to dedicate internal IT staff to the task and minimizes potential loss and liability.
“Regardless of which provider you use, the best tactic to employ is a layered approach with active security monitoring. That way, breaches can be avoided or contained, assets can be protected, and exposure is minimized. When a business is breached, it’s important to ensure that the whole company isn’t incapacitated or bankrupted,” says Eric Brackett of BTI Communications Group, a technology convergence provider that serves the food, logistics, healthcare and aerospace sectors. The company is a single source provider of physical security, access control, network, and complex phone (VoIP) systems, down to installation of wiring and conduit.
As a cost-effective alternative, an IT cybersecurity firm can provide this service on an outsourced basis for pennies on the dollar. For ease of use, all relevant information is provided in a dashboard format that is viewable remotely, with a team of specialists monitoring network conditions and threats in the background.
The end goal for businesses today is to perpetually keep data safe and secure, and operations fully functional, without the risk of a serious hack.
Girish Manglani, head of development at a firm that distributes digital downloadable content, agrees.
“Once corporate data or digital content is on the dark web and sold by cybercriminals, there’s no way to recover your stolen goods at that point. So, it’s important for businesses to be proactive and protect their data so it’s not vulnerable to theft. Executives want to focus on growing the business and taking advantage of opportunities, not fighting off cybersecurity threats,” says Manglani.
He adds, “24/7 monitoring and deterrence against hacking can be achieved by outsourcing IT security to an expert like BTI. It helps to have a team of network security professionals that can remotely assess operations and provide layers of protection for critical data and processes.”