Here at BTI we have a team of experts available to assist you with all your IT, communication, and security needs. Do you want to have the highest security standards available for your company while also reducing costs and increasing your revenue? Contact us now or schedule a free consultation!
In cybersecurity, there are several procedures that need to be checked in order for your security measures to be functional. One of those steps is the CIA TRIAD. The CIA triad is the 3 variables that are needed to design an effective cybersecurity program. Confidentiality, integrity, and availability of the organization’s information and digital assets are needed to follow the “CIA” triad. In the following article, we will discuss what this means for your business.
What is the CIA Triad?
The CIA Triad is an information security concept that consists of three main principles: confidentiality, integrity, and availability. These principles are the core components of information security strategies and solutions. Professional cybersecurity companies and their associates should have a deep understanding and appreciation of the CIA Triad. Every incident presented in cybersecurity needs to be evaluated by how well they address these 3 core principles.
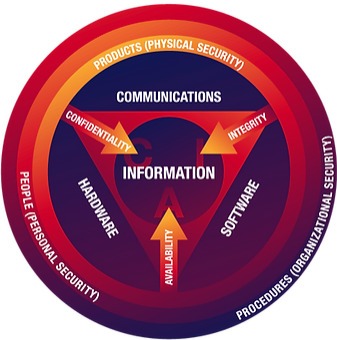
The 3 Core Principles
Confidentiality
This principle is the ability to restrict unauthorized individuals from accessing data systems and other resources. Imagine that an employee forgets to shut down his computer when he leaves the office, later that day, janitorial service arrives at your office and they notice that that computer is turned on and unlocked. Curiosity can be dangerous and even though the janitor may not have bad intentions, having unauthorized personnel access sensitive data can be devastating for your business!There are many types of attacks designed to violate confidentiality. Social engineering, theft of credentials or passwords, and network sniffing are just a few examples. If you want to implement confidentiality in your cybersecurity program there are several control measures that you’ll need to follow.
1. Device and Software Inventory:
An accurate inventory of applications, devices, and systems will make managing your assets easier and more effective. The only way organizations can control who has access to their devices is by knowing how many devices are available and who has access to them.
2. Data Classification:
Understanding what data resides in your system as well as classifying your data in order of importance, value, sensitivity, and regulatory compliance will allow you to have a more secure, reliable, and agile system.
3. Access Control:
Sensitive data should be protected physically as well as digitally. Access to systems and information should be granted exclusively to authorized personnel. A history of permissions granted needs to be followed to have real control of your IT assets. Practices like strong passwords and MFA (Multi-Factor Authentication) should be implemented to ensure the safety of your data.
4. Encryption:
Information is a must for companies that are looking to maintain their data safety. There are a variety of encryption solutions that have affordable pricing and functionality. When you encrypt your information, your data remains confidential!
5. Personnel Training:
Most data breaches occur due to human error. Employees need to be properly trained and prepared to respond, prevent, and deal with cyber threats. Implementing data classification and acceptable use policies allow employees to understand and execute safe data management practices in their workplace.
Integrity
Integrity allows data and information to retain truth and accuracy. Information should not be altered unless it has a purpose behind it. Your cybersecurity program should promote integrity and be prepared to fight against all kinds of cyberthreats. Here are a few controls that will help you maintain high levels of integrity inside your organization.
1. Intrusion Prevention System (IPS) and Intrusion Detection System (IDS)
These tools analyze network traffic to detect and prevent vulnerability exploits.
2. Antivirus and Anti-malware
The main function of antivirus and anti-malware software is to quarantine and remove malicious software that resides inside your device network. These protective measures should be installed in all devices to ensure the protection of everyone inside the network.
3. Vulnerability and Management
Cybersecurity safety protocols be implemented to identify known vulnerabilities and combat them effectively.
4. Log Monitoring and Analysis:
Being able to analyze log applications is critical to maintaining high cybersecurity measures. Managers can detect anomalies and combat suspicious behaviors effectively by implementing these security procedures.
Availability
Availability grants authorized users uninterrupted access to systems and information. Ransomware, for example, is a direct threat to the availability principle because it does not allow employees to have access to the organization’s information. Two other occurrences that also violate the availability principle are hardware failure and natural disasters. Your cybersecurity program should always support the availability principle. Here are some controls that you can follow to maintain this core principle:
1. Data Backup Systems:
Having effective data backup systems is essential to comply with the availability principle. If systems become unavailable, a successful data backup cannot be performed correctly thus hindering business operations.
2. Disaster Recovery (DR) and Business Continuity Planning (BC):
Documenting DR and BC plans will tighten up every aspect of cybersecurity. These plans should be tested annually to verify their effectiveness and make changes as needed.
3. System Monitoring:
Critical systems should be continuously and proactively monitored to prevent unwanted situations.
4. Incident Response Plan
Having a plan to contain, eradicate, and recover from a cybersecurity threat is essential. If people know how to act against a cyberattack, the damage and its consequences can be significantly reduced.